说明
- 操作系统
CentOS-7 jumpserver版本2.0.1。- 根据
jumpserver官方文档里的安全建议,做了以下加固措施- 操作系统保持最新的软件版本
- 仅开放
443和2222端口 - 禁止公网PING响应
- 可是使用一段时间之后,在网页端管理后台,查看
日志审计->登录日志,发现有很多password_failed的日志。 - 登录
jumpserver服务器仔细查看koko的日志后,发现基本都是来自同一个IP地址对多个常见用户名进行暴力登录破解。 - 看来
jumpserver名气挺大的,默认2222端口被暴力登录破解还是挺频繁的,建议修改成其他端口。 jumpserver默认的安全设置只能限制同一用户的登录失败次数、禁止登录时间间隔,这就有点不能忍了。- 于是乎祭出
fail2ban配置自定义过滤器来收拾收拾。 - 这里不仅限于JumpServer,其他应用也可以参考此方法一通百通
安装fail2ban
- 添加EPEL源
1 | yum install -y epel-release |
- 安装fail2ban
1 | yum install -y fail2ban |
jms-koko日志解析
koko的日志文件存放在/opt/koko/data/logs/koko.log这里放一段koko日志的内容
1 | YYYY-MM-DD 20:22:24 [INFO] SSH conn[a521be6ef6f8849382c3e4e3a6ae37b3836ebda0] Failed password for games from 172.105.86.202 |
- 可以看到登录失败的日志格式是统一的以
Failed password for <用户名> from <IP地址>结尾 - 那么可以开始准备配置fail2ban的自定义过滤器了
fail2ban自定义过滤器
fail2ban自带了很多常见服务的过滤器,但是jumpserver不在其中,于是乎自己弄一个吧
fai2ban支持基于正则表达式的过滤,因此可以先用正则表达式匹配一下登录失败的日志
1 | fail2ban-regex /opt/koko/data/logs/koko.log 'Failed password for [A-Za-z0-9]+ from <HOST>' |
- 命令运行之后会显示结果
Failregex: 8234 total代表有8234条记录被匹配Date template hits指该日志中有满足格式的日期
1 | Running tests |
- 既然正则匹配已经ok了,那么就可以配置自定义过滤器了
1 | vi /etc/fail2ban/filter.d/jms-koko.conf |
- 添加如下内容
1 | [Definition] |
配置fail2ban服务
添加fail2ban配置
1 | vim /etc/fail2ban/jail.local |
1 | [DEFAULT] |
检查配置
1 | fail2ban-client -t |
- 输出示例
1 | OK: configuration test is successful |
- 可以通过加
-v或者-d输出详细日志
1 | fail2ban-client -t -v |
1 | fail2ban-client -t -d |
启动fail2ban
1 | systemctl enable --now fail2ban.service |
查看fail2ban的状态
1 | fail2ban-client status jms-koko |
- 根据输出结果可以看到
172.105.86.202已经被ban了
1 | Status for the jail: jms-koko |
查看fail2ban日志
- /var/log/fail2ban.log
1 | 2020-08-30 20:25:33,924 fail2ban.server [1346]: INFO -------------------------------------------------- |
查看防火墙规则
1 | iptables -t filter -L -n -v |
- 输出如下
- 被ban的ip会提示端口不可达
1 | Chain INPUT (policy ACCEPT 779K packets, 71M bytes) |
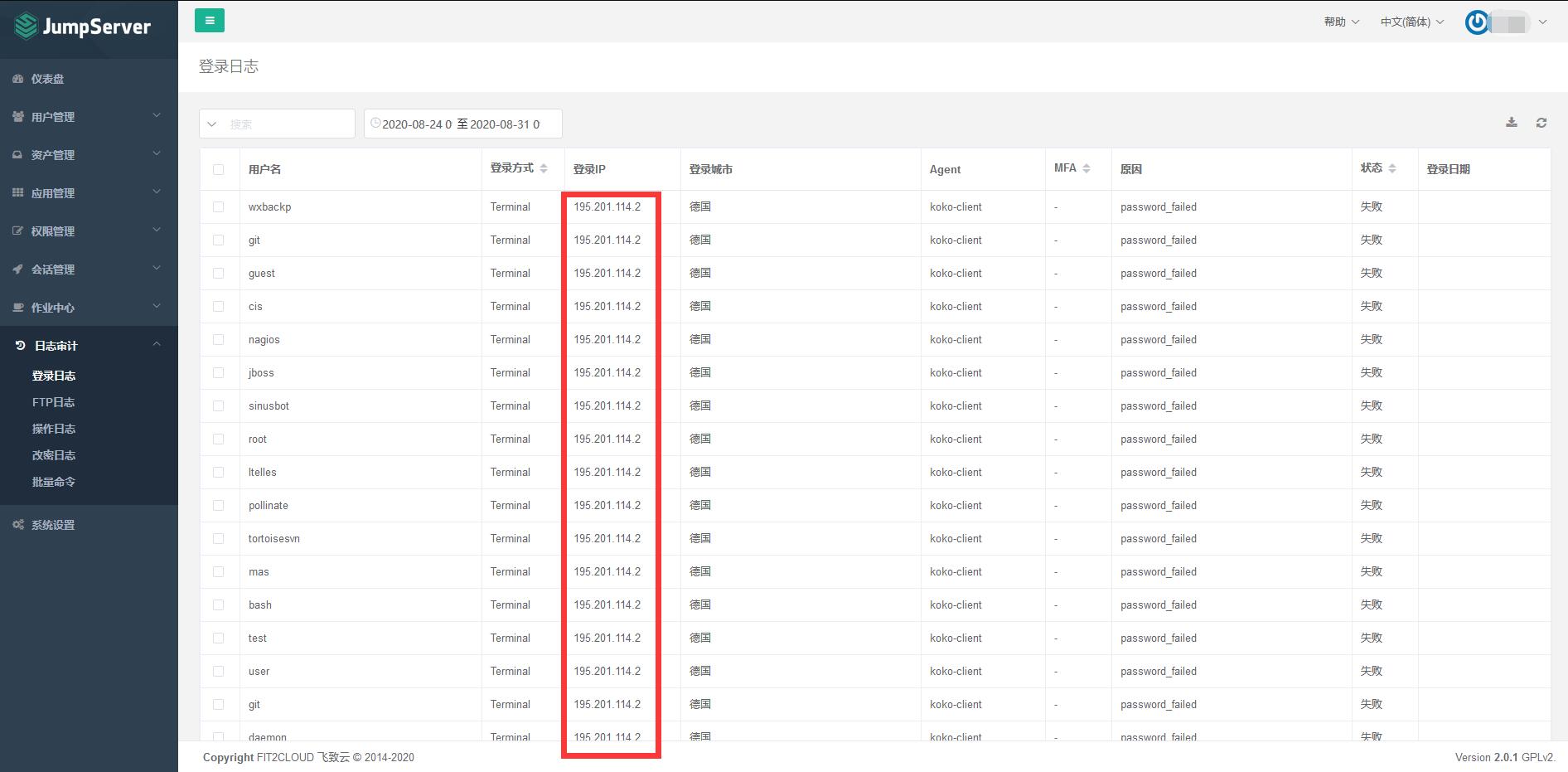
事前
- 根据截图可以看到同一个IP疯狂尝试登录
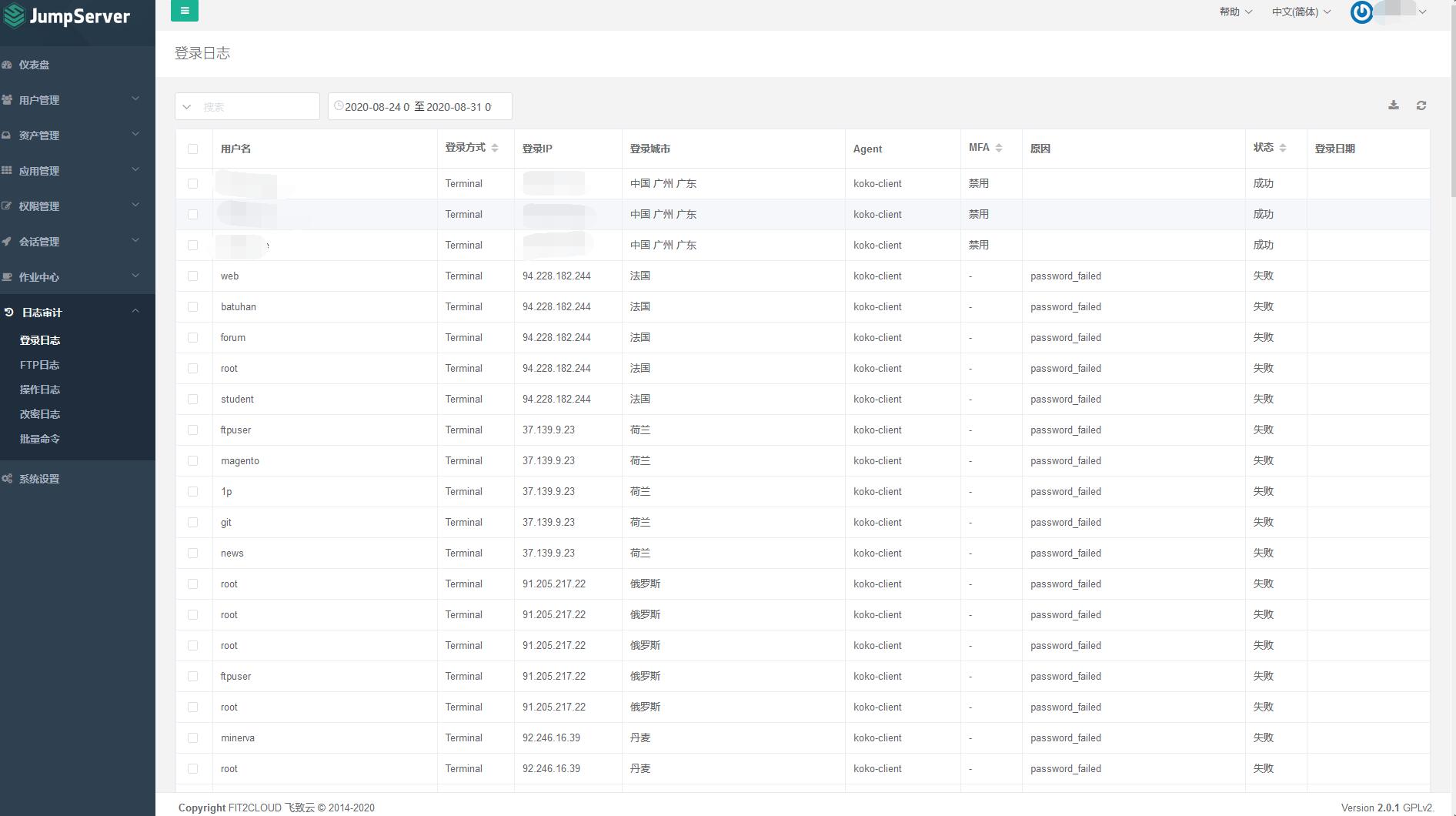
事后
- 一晚上功夫就新增了十几个被ban的ip
1 | Status for the jail: jms-koko |
- 单个IP最多试5次就拜拜了
解封操作
- 说不准有时候会有倒霉蛋输错密码导致IP被ban,可以通过用
fail2ban-client命令解封IP地址 - JumpServer账号锁定的话要在JumpServer里面解锁账号
1 | fail2ban-client set jms-koko unbanip IP地址 |
docker环境配置
说明
- docker会创建两个chain,DOCKER和DOCKER-USE,并且会由这两个chain优先处理数据包
- 其中DOCKER由docker进程维护,DOCKER-USER由用户自己管理
- 默认情况下,通往容器的数据包不会经过fail2ban的chain处理
- 需要修改actionstart和actionstop,将fail2ban的chain插入到DOCKER-USER这个chain里面
- 这样数据包处理路径为 DOCKER-USER ===> f2b-jms-koko ===> DOCKER
添加action
1 | vim /etc/fail2ban/actions.d/iptables-allports-with-docker.conf |
1 | [INCLUDES] |
修改jail.local
- 把
action = iptables-allports改为iptables-allports-with-docker
1 | [DEFAULT] |
重启fail2ban服务
1 | systemctl restart fail2ban.service |
查看防火墙规则
- f2b-jms-koko链
1 | iptables -t filter -n -v -L f2b-jms-koko |
- DOCKER-USER链
1 | iptables -t filter -n -v -L DOCKER-USER |